HP / Aruba Procurve 2530/2500 Default Management IP, Username/Passwrods and Configurations
Back-up of an existing config
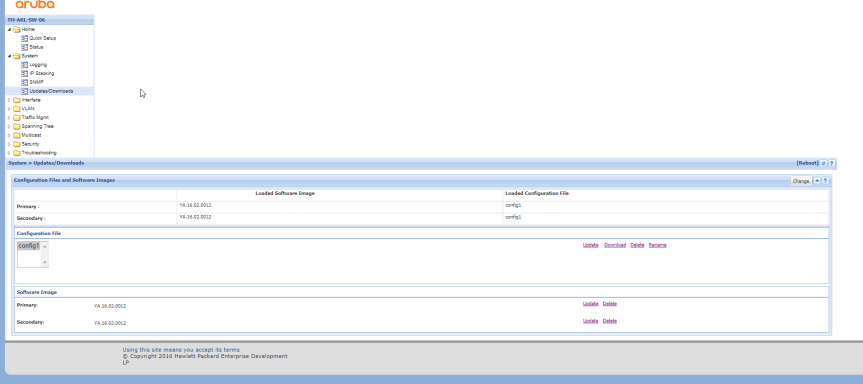
If you are performing a backup a config from another switch, two ways of downloading the configuration is through GUI and CLI (via TFTP)
via GUI: (System -> Updates/Download -> Configuration File (Highlight config name and click Download)
via CLI. (you need to set up a TFTP server on a machine)
switch# copy running-config tftp <IP Address of the TFTP Server> filename.pcc
==============
Default Settings and Configurations of an Aruba/HP Procurve switch
In the factory default configuration, the switch has no IP (Internet Protocol) address and subnet mask, and no passwords. In this state, it can be managed only through a direct CONSOLE connection (How to connect to Console? Click here). To manage the switch through inband (networked) access, you should configure the switch with an IP address and subnet mask compatible with your network. Also, you should configure a Manager password to control access privileges from the console and Web browser interface.
IP-Address
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)# vlan 1
HP ProCurve Switch 2524(vlan-1)# ip address 10.0.0.1 255.255.255.0
HP ProCurve Switch 2524(vlan-1)# wr mem
HP ProCurve Switch 2524(vlan-1)# exit
HP ProCurve Switch 2524(config)# exit
HP ProCurve Switch 2524#
(Basically, from here you can now set your machine’s IP into the same network above and access the GUI from your browser, otherwise, you can proceed with the other commands below)
Also, by default, as mentioned there is no username/password for the switch and you have to configure that manually through GUi or CLI below.
Configure VLANs
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)# vlan 1
HP ProCurve Switch 2524(vlan-1)# name „Default“
HP ProCurve Switch 2524(vlan-1)# untag 2-6
HP ProCurve Switch 2524(vlan-1)# vlan 10
HP ProCurve Switch 2524(vlan-10)# name „First“
HP ProCurve Switch 2524(vlan-10)# untag 7-12
HP ProCurve Switch 2524(vlan-10)# vlan 20
HP ProCurve Switch 2524(vlan-20)# name „Second“
HP ProCurve Switch 2524(vlan-20)# untag 13-18
HP ProCurve Switch 2524(vlan-20)# exit
HP ProCurve Switch 2524(config)# exit
HP ProCurve Switch 2524#
Set up trunk ports
HP ProCurve Switch 2524# config
HP ProCurve Switch 2524(config)# trunk 23-24 trk1
HP ProCurve Switch 2524(config)# vlan 10
HP ProCurve Switch 2524(vlan-10)# tagged trk1
HP ProCurve Switch 2524(vlan-10)# vlan 20
HP ProCurve Switch 2524(vlan-20)# tagged trk1
HP ProCurve Switch 2524(vlan-20)# wr mem
HP ProCurve Switch 2524(vlan-20)# exit
HP ProCurve Switch 2524(config)# exit
HP ProCurve Switch 2524#
Disable all (but trunk) ports
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)# int 2-22 disable
HP ProCurve Switch 2524(config)# wr mem
HP ProCurve Switch 2524(config)# exit
HP ProCurve Switch 2524#
Enable only necessary ports
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)# int 2-4 enable
HP ProCurve Switch 2524(config)# int 13-15 enable
HP ProCurve Switch 2524(config)# wr mem
HP ProCurve Switch 2524(config)# exit
HP ProCurve Switch 2524#
Set up speed etc.
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)# int 2-4 speed-duplex 100-full
HP ProCurve Switch 2524(config)# int 13-15 speed-duplex auto
HP ProCurve Switch 2524(config)# wr mem
HP ProCurve Switch 2524(config)# exit
HP ProCurve Switch 2524#
Set time and date
Time and date on hh:mm and mm:dd:yyyy format
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)# time 10:05
Mon Jan 1 10:05:28 1990
HP ProCurve Switch 2524(config)# time 08/24/2010
Tue Aug 24 10:05:41 2010
HP ProCurve Switch 2524(config)# wr mem
HP ProCurve Switch 2524(config)# exit
HP ProCurve Switch 2524#
Set hostname
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)# hostname „ServerRoom1“
ServerRoom1(config)# wr mem
ServerRoom1(config)# exit
ServerRoom1#
Backup settings
After running “sh run” copy/paste all between line which start with “hostname” to “ServerRoom1#” example to notepad and save that file.
ServerRoom1# sh run
ServerRoom1#
Restore settings from backup
All you have to do is copy/paste all (except the first “Running configuration:” line) to notepad on “Backup settings” part to “HP ProCurve Switch 2524#”.
If you have set operator and/or manager passwords, don’t copy/paste the lines which start with password.
HP ProCurve Switch 2524# configure
HP ProCurve Switch 2524(config)#
Set manager and operator password
ServerRoom1# configure
ServerRoom1(config)# password all
New password for Operator: ********
Please retype new password for Operator: ********
New password for Manager: ********
Please retype new password for Manager: ********
ServerRoom1(config)#
Content retrieved from: https://marktugbo.com/2018/02/20/hp-aruba-procurve-2530-2500-default-configurations/.